Can a hacker decrypt the data encrypted with Stringer?
Stringer employs a highly complex encryption algorithm derived from AES, and scatters the encryption keys, different for each package, across the obfuscated code. It is therefore virtually impossible to create a tool that would decrypt the data automatically, and manual analysis would require a lot of time and effort of a knowledgeable person.
To what degree obfuscation affects application performance?
On average, you can expect your app to lose about 10% of its original performance as a result of obfuscation.
How large is the obfuscated application size increase?
Application code size typically grows by 5% to 20%. There is also an overhead of about 10KB for each obfuscated package.
Can I protect an Android app with Stringer Java Obfuscator?
Yes, you can protect any sensitive information: logins, passwords, public keys of licenses, API credentials, advertising site IDs, links to non-public resources, etc.
We highly recommend using the Stringer Java Obfuscator, especially if you are using Google Play Licensing. The Eclipse plug-in (Stringer@Eclipse Marketplace) makes it very easy to add Stringer Java Obfuscator to your build process.
I have just downloaded an Eclipse plugin of Stringer Java Obfuscator. What do I do next?
This section of the Stringer manual describes plug-in installation and usage procedures in detail. If you need further assistance, please do not hesitate to contact us.
How can I selectively protect particular string constants in a given class?
You need to mark those constants with Stringer annotations. You can also mark methods and (inner) classes.
By default, i.e. when no Stinger annotations are present, the entire class file is protected.
Please refer to the manual for more information: Using annotations.
Why does Stringer encrypt only strings in class files (string encryption) rather than the entire class files (class file encryption)?
Class file encryption only protects your app from hackers that manage to get hold of your code but not the decryption key. In all other scenarios, it is nearly useless, as the JVM can only load decrypted classes and retrieving class files from a running app is trivial. Furthermore, a custom class loader responsible for class decryption may clash with other custom class loaders, commonly found in Java application servers, ultimately leading to an application failure.
Selective encryption of string constants within class files, combined with Stringer's call context check functionality, is a safer and more secure option.
See also Protect Your Java Code — Through Obfuscators And Beyond, A Gun is a Great equalizer: OpenJDK Hack vs. Class Encryption
Can I protect an Eclipse RCP application with your obfuscator?
Sure.
First, you need to download and install the Stringer Java Obfuscator Eclipse plug-in (Stringer@Eclipse Marketplace).
Upon completion of the installation, open an RCP project or create a new one and go to project settings. Then select Builders and add Stringer, it should be located right after the Java Builder (For more information see the manual: Installing and using the Eclipse plug-in)
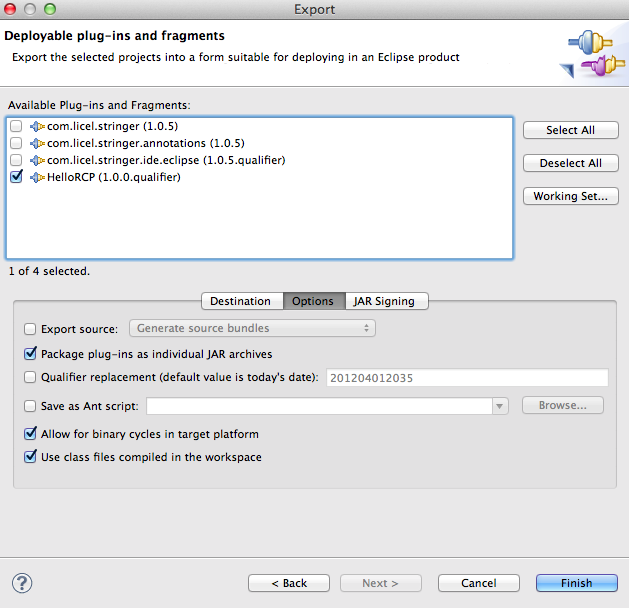
Finally, select the checkbox "Use class files compiled in the workspace" in the Options tab of the Export Dialog Wizard and Stringer will protect your application when you export it.
I am unable to activate my Stringer Java Obfuscator license. What's wrong?
The most common cause is that Stringer cannot connect to the licensing server.
- If you are using a proxy server, check the proxy server settings in the JRE.
- If you are behind a firewall, make sure that it does not block outgoing connections from the JRE.
In other cases you may use the offline activation mechanism.